This article will explain why DDoS attack mitigation is a necessity for enterprises looking to protect themselves. We’ll take a look at the past, present, and future of DDoS, and how you can navigate these attacks to not lose your organization money.
The first DDoS attack occurred in 1997 during a DEF CON event in Las Vegas. The culprit was notorious hacker Khan C. Smith, who successfully shut down Internet access on the Vegas Strip for over an hour. The release of some of this code opened up a can of worms and soon led to online attacks against Sprint, EarthLink, E-Trade, and many more corporations. Later in 2001, Smith would go on to create the first botnet, which was responsible for 25% of the entire Internet spam at the time.
Fast forward two decades later to March 5, 2018, where an unnamed customer, with the help of NETSCOUT (formerly Arbor Networks), battled the largest DDoS in history, reaching a peak of about 1.7 terabits per second. This broke the previous record, which occurred just 3 days earlier, where GitHub was knocked down by a 1.35 terabit per second attack. Before 2018, there was never an attack higher than a terabit.
DDoS attacks have been around almost as long as the Internet, yet enterprises are not only struggling to protect themselves, but encountering attacks the breadth of which has never been seen. It’s no longer a matter of if your business will fall victim, but when. So what happens now?
The Current State of DDoS Attacks
Memcached Servers Help Create Largest DDoS Attack Ever: That GitHub attack originated from over a thousand different systems across tens of thousands of different endpoints. This was an amplification attack using the memcached-based approach. Memcached is free software that speeds up database-driven websites by caching data in RAM to reduce disk strain.
Hackers exploited a UDP vulnerability and ended up flooding valid requests to an exposed Memcached server. This attack has a 10,000:1 amplification ratio, so on average, every byte an attacker sent to the exposed Memcached server, the server would then send 10 KB to the actual victim.
Here at HostDime, we saw evidence that servers on our network could be directly affected and immediately blocked all packets with a UDP destination port of 11211 from entering our networks.
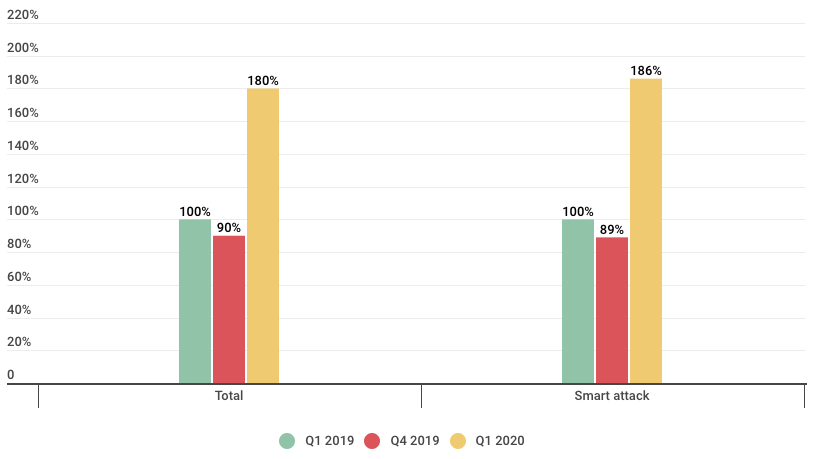
DDoS Attacks Growing in Quantity and Quality: It was all bad news in Q1 2020. While humanity continues to deal with the coronavirus pandemic, hackers did not take a break. Q1 2020 saw a huge increase in both size and total number of attacks. There was a significant rise in the length of these incidents, in both average and maximum duration. The amount of attacks actually doubled versus Q4 2019, and 80% higher than Q1 2019.
It’s Costly to Get Attacked: How much money should a business expect to lose when they’re hit with a DDoS attack? DDoS defense company Corero Network Security sought to answer that question and polled 300 security professionals from cloud, government, finance, media, and online gaming. Here are the not-so-uplifting findings:
- 91% of those surveyed said that DDoS attacks can cost their organizations up to $50,000.
- 85% believe that DDoS attacks are used by attackers as a precursor or smokescreen for data breach activity.
- 71% reported that their organization has experienced a ransom-driven DDoS attack.
- 78% cited the number one most damaging effect of a DDoS attack is the loss of customer trust.
While not all DDoS attacks are going to cost 5 figures, what may be worse is having your website inaccessible and ruining customer confidence. A company’s reputation can be linked to corporate profits.
What’s Next?
Rise of the IoT Botnets: What a world we live in when your refrigerator is hackable. Khan C. Smith’s spammy e-mail botnet has evolved into an Internet of Things botnet that shows no signs of stopping. Here’s Guy Rosefelt of cloud security company NSFOCUS on his main IoT security concern:
“As IoT innovation continues to blossom, more and more IoT devices will continue to get involved in DDoS attacks. Routers and cameras are the major types of IoT devices involved in DDoS attacks, with routers making up 69.7% of IoT devices exploited to launch DDoS attacks, and 24.7% of cameras. This is because a great number of routers and web cameras have been introduced into production and living environments, with no sufficient security measures enforced. We have every reason to believe that attacks leveraging the IoT will become more diverse in the future.”
As these IoT devices become outdated, vulnerabilities will surface and become an easily exploitable weapon. These devices take much longer to patch than Operating Systems, so these attacks often last longer.
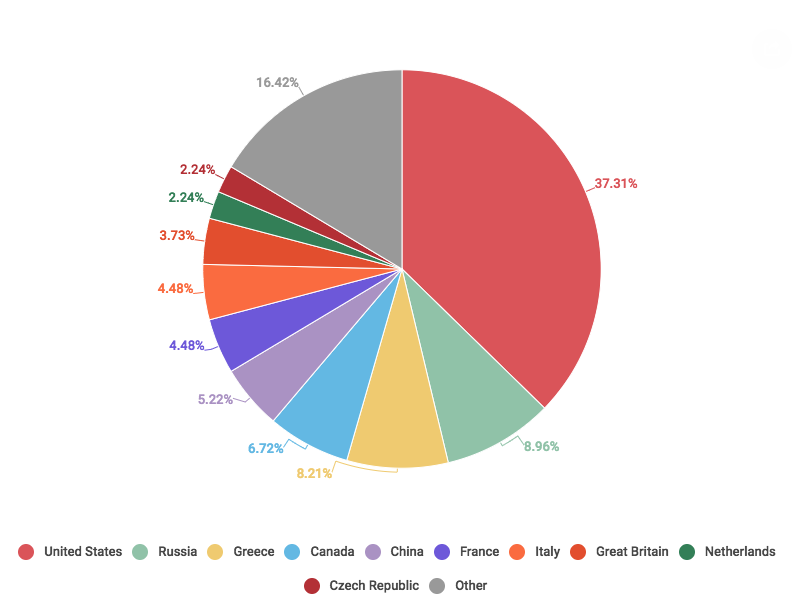
Thanks to information and the below graphic from Kaspersky Lab, we can see the US leads the world in botnets, with Russia in second. More countries’ botnets are being exploited like never before, as hackers aim for geographic redundancy.
The CoAP Protocol: Oh fun, another amplification attack is here. CoAP, or the Constrained Application Protocol, can be thought of as a layer on top of the Internet of Things that handles congestion control. The CoAP protocol is a newish breakthrough that plays a role in speedy machine to machine communication among both consumer and industrial applications. However, with this newness and lightweight protocol, comes a chance at exploitation.
CoAP uses UDP, which like the memcached servers, is vulnerable to the type of IP spoofing and packet amplification that enable large DDoS attacks. As aforementioned, this can cause huge amplification attacks spoofing 10 to 50x the normal amount of traffic.
CoAP devices have become all the rage lately, going from 6,500 devices in November 2017 to now over 600,000! ZDNet has recently reported from an anonymous source that over half of these devices could be used in DDoS amplification attacks and attacks have already begun, with increasing frequency and size.
This won’t be an easy fix, as we are accustomed to speed, especially with the IoT, and it looks like we will have to sacrifice some of the speed for security, or perhaps stop using these CoAP devices altogether.
Pro tip to anyone with IoT devices in their home or office. While it’s not much, be sure to change the default username and password, and be on the lookout for suspicious activity and patch updates. There seems to be a shift to using outdated devices to launch these attacks. Let’s hope this isn’t what the near future looks like:
DDoS Attack Mitigation Services
Do you have the latest DDoS fighting tools and technologies ready for 2020? You can’t predict how large an attack against your server will be, however you can choose what protection you need based on how mission critical your operations are.
HostDime’s secure network is among the most DDoS protected in the infrastructure industry. That’s because we offer three types of DDoS protection: NETSCOUT’s local inline mitigation, a cloud-based traffic scrubbing service, and a combination of the two with our hybrid protection.
The NETSCOUT appliance sits within our facility for inline protection. When the appliance detects irregular traffic, our team moves the affected subnet and begins filtering. With our Cloud Scrubbing service, ALL traffic gets filtered through one of our various GRE tunnels. Our Hybrid DDoS is unique for its performance based, “always on” protection. Read on for a more in-depth look at the intricacies of each service.
Inline DDoS Protection
HostDime offers premium hardware-based DDoS monitoring and mitigation, while most service providers offer reverse proxy DDoS detection. The problem with this is your traffic goes to a third party, is cleaned, then re-routed back to your host.
Our DDoS protection is different because it’s inline, or actually within the data center. We take both your affected and unaffected traffic, filter out the bad stuff, and leave only legitimate traffic flowing to and from your server. Once a server is placed behind our DDoS protection hardware, it learns “normal” traffic patterns so it can identity bad traffic in the future. Therefore end users notice no added latency, even when active mitigation is taking place.
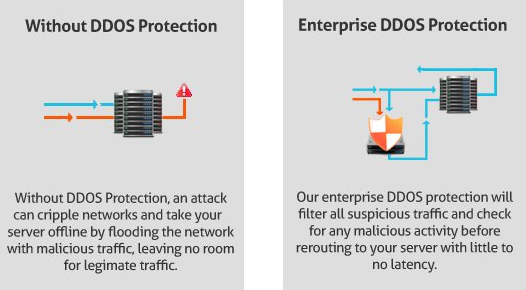
Cloud DDoS Protection
HostDime’s DDoS Cloud Scrubbing is a IP routing service where all traffic is examined and filtered, then the cleaned traffic is forwarded to our enterprise network via our Generic Routing Encapsulation (GRE) tunnels. This security cloud is a private point-to-point link between network nodes, and acts as our safety net if a large DDoS attack occurs. Your whole critical infrastructure is safe with this protection.
Here is a visual depicting how HostDime’s global security cloud delivers clean traffic to a visitor accessing a DDoS affected website.
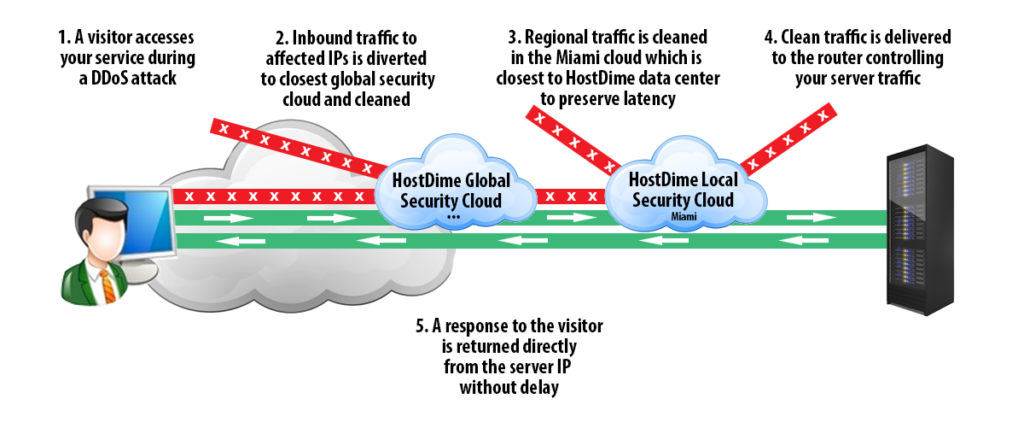
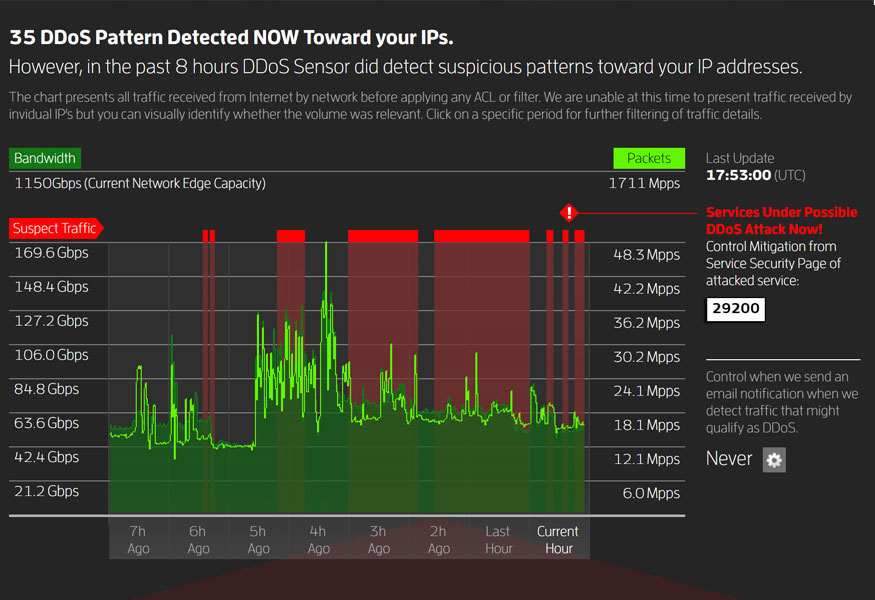
All IP addresses routed through our scrubbing centers are protected against DDoS attacks. The always active service uses network sensor devices to immediately detect suspicious patterns. Traffic toward that IP is then redirected for mitigation in our security cloud. Redirection stops minutes after the attack ends. HostDime’s DDoS protected GRE tunnels can clean an attack up to 100Gbps; that’s an impressive amount of scrubbing power.
Hybrid DDoS Protection
Lastly, HostDime’s Hybrid DDoS Protection gives clients the best of both worlds with a performance based option with “always on” protection. This unique set-up combines the inline DDoS protection appliance with the DDoS cloud filtering service. This protection detects and acts immediately against all sorts of large and complex attacks. When disruption occurs, clean traffic still gets through thanks to the cloud scrubbing. One difference between this service and the cloud scrubber is added latency when in protection mode.
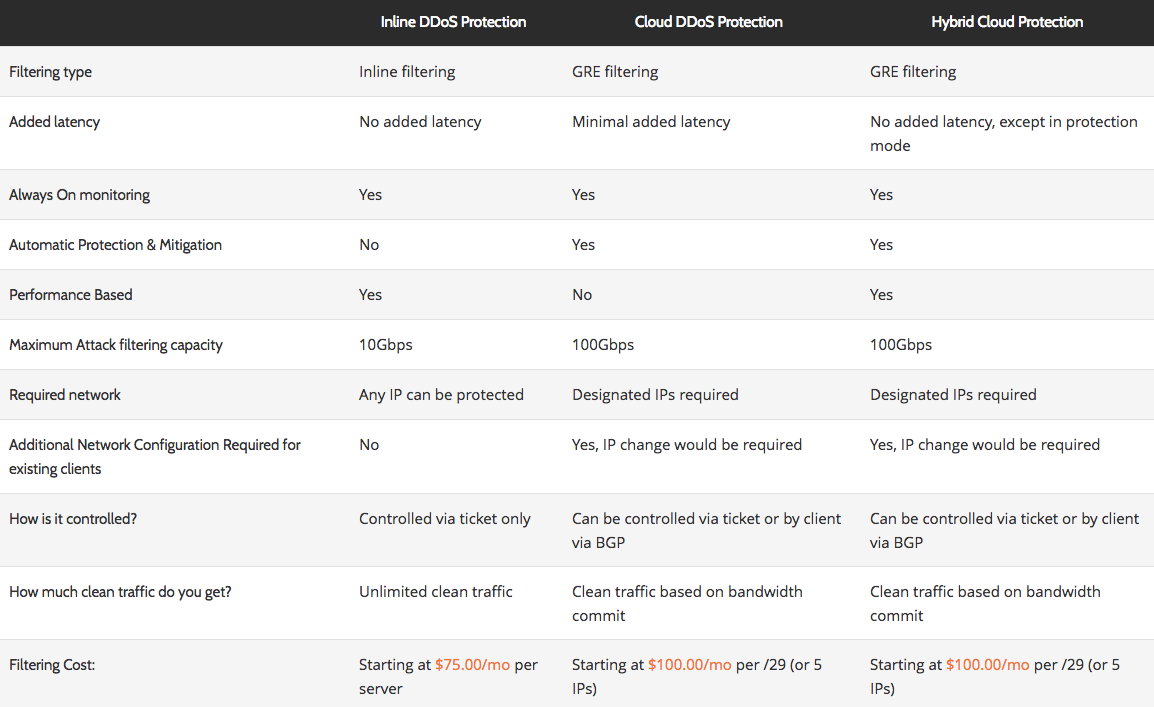
The following chart spells out the differences between the three DDoS protection services. Whichever you choose, enjoy peace of mind knowing your business will have superior uptime, uninterrupted data center access, and relief from network security threats.
HostDime’s inline DDoS service is included on all managed dedicated servers, but if you require additional protection, contact us now to figure out the right plan for you. We offer both monthly and on-demand packages, featuring over 5GBPS of attack protection if necessary. Currently, only dedicated server and colocation clients can take advantage of these additional DDoS protection services.
Stay safe out there!
[divider]
Jared Smith is HostDime’s Content & SEO Strategist.